Cybersecurity: No One Is Immune

Guest Post by Ed Berush
Ed Berusch serves as a consultant and trusted advisor to CIO’s and CTO’s with the goal of Simplifying their IT environment. Through my work you can Get IT Faster, Run IT Better, and Grow IT Smarter.
Disclaimer: I work for Dell Technology Services. It is my passion to help guide organizations through the current technology transition we call the Digital Transformation specifically as it relates to Workforce Transformation. Visit Dell Technologies site for more information. Opinions are my own and not the views of my employer.
Today I write about the uptick of recent cybersecurity incidents reported in the news as of late. The list is long and it has affected business of all sizes and in all industries. The sophistication of the attacks, and vulnerabilities they uncovered are only one side of the coin. Many of them are now truly affecting many lives, and livelihoods.
And the situation is now criminal entities are much more organized, and have developed a business model, they can replicate and sell to whoever needs it.
DarkSide first came into light in August 2020 and was initially conducting its own ransomware attacks. By November, the group and 14 other such criminal gangs were responsible for more than 1,200 ransomware attacks, according to Intel471, which tracked 25 different RaaS groups throughout 2020.
Ransomware is booming as a business model: “It’s like eBay” – CBS News
The world is getting hacked, no one is immune.
Cybersecurity should be at the center of every IT conversation out there.
A few facts first:
- According to Hosting Tribunal website report, there is a hack every 39 seconds ( Many go unreported )
- It’s not just the big guys getting hit. K-12, local governments, small businesses and commercial customers
- The call from help can come from anywhere – A friend, a peer, a friend-of-a -friend, Director, CFO , CEO.
- Unfortunately, ransomware business has become a lucrative criminal business model ( read here )
- Last week, the US Government, called for the federal government and private sector to partner to confront “persistent and increasingly sophisticated malicious cyber campaigns” that threaten U.S. security (Article | press release ).
A Sample List
A sample of the 22 reported breaches in May 2021 is listed below. — Yes in one month, not all year. Here is a partial list of the most notable ransomware attacks:
- We begin the month in Switzerland where cloud hosting provider Swiss Cloud [securereading.com] were the first to report a ransomware attack. The firm did not reveal details about the incident but they did disclose that they were working in 24-hour shifts, including weekends to restore service. Payroll giant Sage, one of their most high-profile customers was affected by the outages.
- Healthcare giant Scripps [bleepingcomputer.com] was next to report an attack. The San Diego based non-profit healthcare provider was forced to suspend user access to its online portal and switch to alternative methods for patient care operations while some critical care patients were redirected to other facilities following the attack.
- Volue Technology [itwire.com], a Norwegian based leading supplier of technology was a victim of RYUK ransomware. The firm took a different approach to disclosing the incident as they set up a webpage with information and updates relating to the attack. The telephone number and email address of their chief executive was also included, urging people to get in touch with him if they needed more information.
- The most high-profile attack of the month goes to Colonial Pipeline [bleepingcomputer.com], the largest fuel pipeline in the US. An attack from the DarkSide ransomware gang caused havoc throughout several states in the US as the outages caused a shortage of gas. The company opted to pay a $5 million ransom so services could be resumed.
- The City of Tulsa [bleepingcomputer.com] in Oklahoma were forced to shut down their systems and online services following a ransomware attack. The incident did not disrupt emergency services but it did impact online billing for residents. The city has said that customer information had not been compromised in the attack.
- Yamabiko [infosecurity-magazine.com], a Tokyo based manufacturer of power tools and agricultural and industrial machinery was targeted by the Babuk ransomware gang. Although the company had not officially confirmed the attack, the Russian based cybercriminals released some of the exfiltrated data on their leak site. They claimed to have exfiltrated 0.5TB of data from the firm.
- Germany headquartered chemical distribution company Brenntag [bleepingcomputer.com] paid a $4.4 million ransom in Bitcoin to the DarkSide ransomware gang in order to receive a decryptor for their encrypted files and to prevent the threat actors from publicly leaking the exfiltrated data. The cybercriminals claimed to have stolen 150GB of data during the attack. A screenshot including some stolen data was shared on their leak site.
- The Health Service Executive in Ireland [news.sky.com]announced on Twitter that they had experienced a ‘significant’ ransomware attack which forced the shutdown of their systems as precaution. All outpatient appointments were cancelled. The Conti gang set the ransom at $20 million in exchange for decrypting the data and deleting 700Gb of unencrypted files that they had exfiltrated during the attack.
- After insurance giant AXA [bleepingcomputer.com] announced that they would be dropping reimbursement for ransomware extortion payments for cyber-insurance policies in France, some of their locations in Asia including Thailand and Hong Kong were hit by ransomware. The Avaddon ransomware group claimed responsibility for the attack and revealed on their leak site that they had exfiltrated 3 TB of sensitive data from the company’s Asian operations.
- Visalia Unified School District [kmph.com] in California revealed they had experienced a Ransomware attack which knocked many of its district IT systems offline. A press release issued by the district did not specify if any student or teacher information was compromised during the attack.
- Waikato District Health Board [rnz.co.nz] in New Zealand suffered a ransomware attack which is thought to have started via a malicious email attachment. The attack downed computer and phone systems and forced staff to resort to pen and paper. Patient surgeries and outpatient appointments were also cancelled because of the incident.
- The Rockland Public School District [boston25news.com] in Massachusetts became the next education victim. A notice from the school said no student Chromebooks had been affected but laptop and desktop access for staff was not possible. It’s not known who was behind the attack.
- Texas based homebuilders Betenbough [kcbd.com] scrambled to try and protect their clients after Russian hackers leaked personal information following an attack which saw the criminal gang hold the developers data to ransom. After hiring a cybersecurity expert to help deal with the incident, the company revealed that some sensitive client data had been posted on the Dark Web.
- Toyota [theregister.com] made news next when they disclosed that they had been hit by two cyberattacks, the first of which hit its subsidiary Daihatsu Diesel Company, meanwhile, numerous Japanese media outlets reported that US subsidiary Auto Parts Manufacturing Mississippi had revealed a ransomware attack. Reports said that some financial and customer data had been exfiltrated and exposed but the company had not paid a ransom and had not been disrupted.
- Insurance broker One Call [insurancetimes.co.uk] in the UK were hit by the Darkside gang who allegedly set a ransom of £15 million in exchange for not leaking the firms data. The Doncaster based firm have not yet revealed if any customer data was exfiltrated during the attack.
- Audio giant Bose Corporation [bleepingcomputer.com] disclosed a data breach following a ransomware attack that hit the company earlier this year. A company spokesperson said that the systems were recovered quickly, no ransom had been paid and that an investigation revealed a small number of affected parties who had been notified. The investigation also found that some employee data had been exfiltrated but had not been leaked on the Dark Web.
- Sierra College [insidehighered.com] a Northern California community college was hit by ransomware which affected the college website and some other online systems according to a statement posted by the college. The college is working with third-party cybersecurity forensics experts and law enforcement to investigate the incident.
- ParkMobile [krmg.com], a Tulsa Oklahoma firm that manages the city’s downtown parking via its app altered users of a ransomware attack. The company disclosed that the incident was linked to a third-party software vendor. The attack was not related to the earlier attack on the City of Tulsa.
- Clover Park School District [kiro7.com] in Washington was the next victim in education. The hackers threatened to release the exfiltrated data unless a ransom was paid. A screenshot of the message said “Clover Park School District, you’ve been hacked,” “Pay or grief. Sensitive information will be shared to the public … There are (not) any third-party solution(s) which can help you. But you can damage your information”, was shared was local news.
- The Azusa Police Department [latimes.com] in Southern California became a victim of the DoppelPaymer criminal gang who exfiltrated data and followed up with a ransom demand. Officials of the city of 48,000 residents decided to keep the attack a secret for 2.5 months before disclosing that data compromised in the attack “may have included” social Security numbers, driver’s license numbers, medical information, financial account information and other records. The cybercriminals posted 7 GBs of Azusa records on the Dark Web.
- The next reported attack of the month was on the world’s largest meat processing firm JBS Foods [bleepingcomputer.com]. The company was forced to shut down production at several global sites following a cyberattack. JBS USA issued a press release on May 31 confirming that the attack had impacted their North American and Australian IT systems. At time of writing the nature of the attack is still unknown while the investigation continues, but cybersecurity experts believe there is a high chance that ransomware was involved.
- The last attack for May hit backup appliance specialist Exagrid. [computerweekly.com] The Conti cybercriminal gang were behind the attack which exfiltrated employee and customer data, confidential contracts and source code. A ransom of $2.6 million was paid to
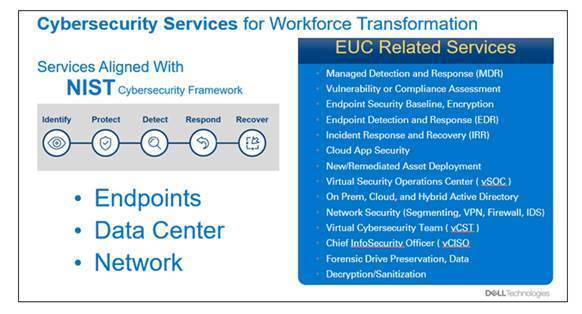
My company Dell Technologies has multiple types of products and services to help our customers mitigate, reduce risk and more importantly recover from a breach.
Check out Dell Technologies Security Transformation for more information.