Transcript of YouTube Video Originally posted on this blog
We live in an interconnected world. People, companies, groups, friends all intermingled with each other. They all interact with each other.
We are constantly exposed to cyber-attacks from individual hackers to highly organized groups including state sponsors that were seeking to either grab certain information or simply seek to disrupt the organization.
Attacks can vary widely and the most common one out there you hear in the news is ransomware attacks, however, they range widely anywhere between Malware, Phishing, Distributed denial of service, Man-in-the-middle attacks, Rogue software, Malvertising, Password attacks of all kinds. Each one of these attacks has a different target, it has a different end-user in mind, it has a different DNA and they can be combined to successfully penetrate those target customers.
One more thing to note is that these kinds of attacks may not be in media, bad actors can play deeds inside organizations which will trigger based on certain actions, much later a remote
call even though the seats have been placed there months or years before.
What is Cybersecurity?
Cybersecurity is the body of technologies, processes and practices designed to protect networks, computers, programs and data (data key components) from attacks, damage or unauthorized access.
What are we supposed to do from this perspective? There are many kinds; multi-faceted, multi-layered integer simple pieces to protect our data, computers, networks and programs, these include;
- Application security
- Network security
- Information security
- Device security and
- Operational security
They are all part of the group of practices that focus on protecting those specific sections of Information Technology (IT) infrastructure.
There are key components that include disaster recovery, business resiliency, business continuity and incident response plans. All of these need to be underlined by the continuous end-user education and awareness that these things are happening, and how to identify potential threats.
For instance, if I receive an email from a very good friend that says “Hey have you seen my photos.” If I didn’t know any better, I would have clicked on that and it takes me two seconds. Another similar example is a very valid Facebook page where I enter my credentials because I thought I wasn’t necessarily logged on, and it was a phishing site that looked very much alike, so if I wasn’t trained in identifying those, I would have gone ahead and clicked on it provided my user credentials then the bad actors go-ahead to collect all that information, put it in a package and then sell it in the black market. All that information is easily captured by unaware and uneducated end-users.
Hence, end-user education is very important to that problem.
There are three pillars to Cybersecurity;
- People: people are ultimately the ones that will stop identifying those threats.
- Processes: What do you do with those alerts? What is happening? How do I report that to somebody? How do I let know that I either clicked or didn’t click on the arrow?
- Technology: Some technologies enable it to automatically identify and quarantine those elements.
Most people, organizations and individuals depend on these elements. However, the true success of a good cybersecurity partner is to balance this between the knowledge of people, the knowledge of the process or the implementation of processes automated away from the technology side of the house. I know we have very good technologies but it takes all three elements to make that happen.
There are many frameworks such as NISE, COBIT, NERC and models like the CSF HITRUST M model that are available out there which help organizations assess and also act on these threads that help many organizations implement all three cybersecurity elements. Some focus on compliance while some focus on maturity. Therefore, it’s important to understand the most common one, which is NISE.
In the ITIL framework, and as it relates to cybersecurity, attacks are called incidents. Some events happen prior to an incident that can alert you to the fact that an incident is happening. This incident response plan will take effect based on the incident. There is a lot of confidentiality and disclosure that needs to happen when an incident happens within organizations. There’s the stigma of being attacked, the loss of business and so on that need to be included in an incident response plan.
The Challenge at Hand:Discovery to Recovery
The challenge at hand is how an IT organization discovers and what it takes to recover. That infection discovery to recovery time is what is called the Dwell time. When an
incident is discovered, there is a certain amount of time that is required to detect or discover an incident. That’s the first part of the line called Media Time to Detection(MTD). Once it’s discovered, incident recovery plan starts to happen, then there is a Media Time to Recover (MTR) and those two pieces are very important for the full recovery of the organization.
This time, combined Media Time to Detection and Media Time to Recover has been touted anywhere from 56 days to 150 days in past years.
Today, if you look at the incident recovery time or cybersecurity recovery time, you will notice based on some studies by IBM, others are 280 days. This is very important because it shows the sophistication of the attacks, how long and how sophisticated these attacks have had from hackers and bad actors out there. That IBM report listed in the above image is fascinating because it also talks about the cost of those attacks and the bottom line is that these companies may be losing lots of money through that process because each day of non-functioning is a day of lost income so organizations need to be able to understand this.
Terminology:EDR/XDR/MDR
What is Security Information and Event Management (SIEM)?
These are the systems that provide real-time analysis of security layers generated by the hardware or the software within an organization. A SIEM is what is used to monitor and detect event signs and it’s a logic, in that SIEM is able to automatically identify what may seem very different alert points.
If you look at it individually, they don’t mean anything but if you look at it as an aggregate, they collect the information and “there is a good example would be firewall got down, then immediately after six other servers and 15 computers went down, so individually on an organization with a hundred thousand devices and several thousand servers that may not mean anything but indeed that combination of events can be identified and there’s no human person that will be able to identify those. That is where artificial intelligence comes along and that’s what it’s able to provide, then collect that information, make it an incident that can be responded to. Beyond that being able to execute a workflow that has been agreed upon on those components.
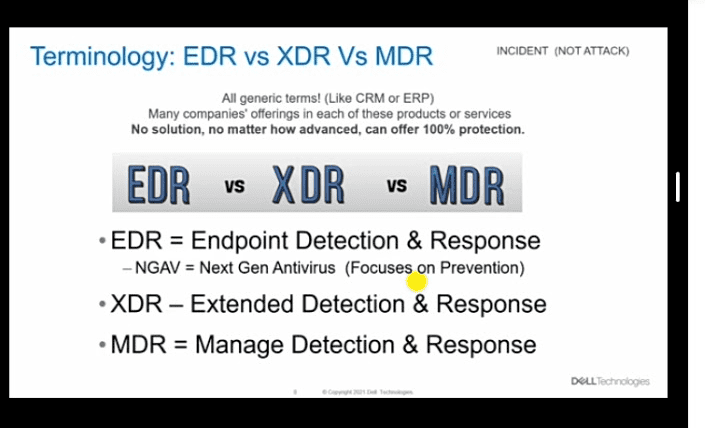
Now, attacks for security experts are called incidents. Instead, the terminology associated with this is EDR versus XDR versus MDR and these are all generic terms, just like CRM, just like ERP. Many companies are offering each of these kinds of products or services and there are many names associated with it. For example, for EDR will be Mc Afee, Crowdstrike, Falca. XDR will be secure work stages Palo alto, Cisco, even Microsoft is the business of EDR and XDR. EDR is an Endpoint Detection and Response Service which is a level up from next-generation antivirus, which focuses on prevention alone. The XDR is the Extended Detection and Response System that you are going to be utilizing.
In addition, Endpoint Detection and Response Service focus on endpoints while Extended Detection and Response System collects information from all systems, network, devices, application systems. It really takes a holistic approach to monitor your environment.
Also, on each one of these response conversations, response on an EDR may be a workflow or an automated component. For example, if a device had a next-generation antivirus or an EDR detection system what it will do if it detects malware is that it’s going to take it, put it in quarantine and not be allowed to exit from the quarantine area. That’s an automated system or automatic process, that’s the response. It’s the workflow you’ve defined. If this happens, then the system knows what to do, you can do the same with an extended detection and response piece. It is automated systems workflows that you create or buy from specific vendors in certain cases and then you need to spend a lot of time internally in defining what those workflows would be, defining what those use cases and cases will be. If this happens, then do this and that. This is what the system is capable of doing.
Now, Manage Detection and Response (MDR) on the other hand, you have people that are monitoring the XDR environment because they collect the aggregation of all of those systems and then they have people that it’s monitoring and looking at the alerts and refining those based on the aggregation of all the customers that particular manage detection service. One of the largest out there is Microsoft, Crowdstrike etc. Many organizations have this and they are continuously tweaking those pieces. The response side of the house is not only a workflow or automated workflow but also is a hands-on keyboard hands-on set. If an incident happens
and you require an incident response team to be on-prem to manage that response, you will be able to have that as part of your manage detection and response service, so very important
differentiator between the tools. The technology size which is EDR, XDR versus MDR
where you have people that are dedicated to that pieces while in the EDR and XDR, you will
be implementing technology and then you need to staff it with the team members versed in not only alerts and incidents, but they need to be alerted into all the different systems hardware because of alerts, application, monitors and logs that you are managing detection and response services is what they are attending. The world is moving to cybersecurity fundamentals.
In my blog post in which you are going to find more information and some reference links associated with it at my modern blog site additionally. Please feel free to check the Dell Technology Security Solutions website as well as our managed detection and response service.
Dell Technology cybersecurity services has a complete offer ranging from endpoints to the data centre and network and applications. The services are aligned with the NIST cybersecurity framework. Dell Technology Cybersecurity services range from managed detection and response services to endpoint protection as well as virtual staff or staffing services as well as cyber vault services or business resiliency and business recovery components. We also have a strong bench of cyber security advisory team members, and we are here ready to help, of course, we have the best of class incident response and recovery team which can help you recover from any kind of incident out there which is also aligned with the zero-trust security framework which is never trust always verify component. We look forward to talking to you.
Thank you very much for listening to this session of explanation.
I am Jorge Pereira, one of Workforce Transformation Solutions Principal for Dell Technology Services.
