Windows 10 Refreshing the OS – Operational Processes

Guest post by Colin Sainsbury
About Colin Sainsbury With over 20 years of experience in the IT industry, Colin provides strategic guidance and technology expertise that organizations need to transform their end user computing environments. He works at Dell Technologies Services as a Principal Consultant supporting global customers. Twitter | LinkedIn |
In the past, operational process often involved to wiping and reloading/re-imaging a device between users or to fix issues that have crept in. This is both time consuming and costly representing an unnecessary overhead. In environments where contingent/contractor labour is a high proportion of the workforce, this has been a significant cost driver. Windows 10 provides new ways to address this challenge.
It should be noted that none of these approaches deliver true data sanitation nor do they claim to be NIST 800-88 compliant. In this sense, they might be appropriate between users within the same organisation or business sub-unit but not when end of warranty devices are being returned to lessor or sold on. Always take advice from your information security team before adopting one of these methods to ensure that it meets their need to protect your data.
1) Consumer Option
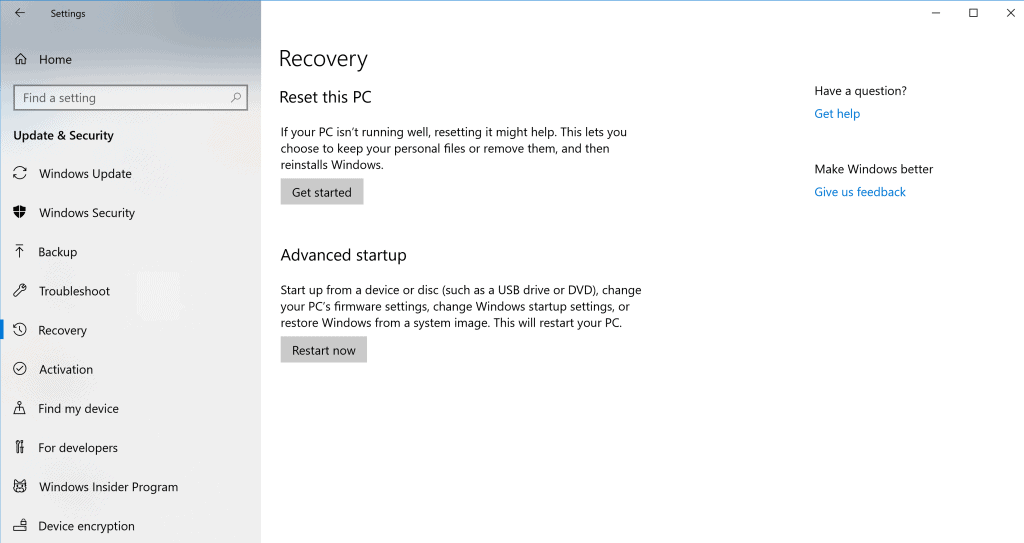
Start/Settings/Update & Security/Recovery/Reset
This capability is aimed primarily at the consumer market and probably should be disabled in the Enterprise space. – It offers two options:
- Keep my files – this removes applications and settings but not data and is useful when a recent application or driver install has upset the status quo. This would be used in a scenario where the device is being returned to the same user.
- Remove everything – guess what this does! This would be useful when transferring the device between keepers. Care should be taken with devices that contained sensitive data to ensure that there is no inadvertent data leakage to the next keeper.
2) Windows Autopilot Reset
Windows Autopilot Reset relies on Windows 10 version 1709 and above (W10 1709+), with Windows Recovery Environment enabled, Autopilot, Azure AD P1 and Intune – again with two options
- Engineer reset (W10 1709+)– this capability must be explicitly enabled. It allows an engineer to trigger a Remove Everything wipe whilst retaining Autopilot enrollment. The engineer executes a three-key sequence (Ctrl+ Windows Key +R) and is then prompted to authenticate.
- MDM triggered (W10 1903+)– Use of an MDM (e.g. Intune) to remotely trigger, via network connectivity, a Remove Everything wipe whilst retaining Autopilot enrollment. Only supported on devices that were enrolled using Autopilot user-driven mode.
3) Windows 10 Enterprise Reset
Windows 10 Enterprise Reset for Workspace ONE – equivalent to the MDM triggered approach above, keeping either the Autopilot or Workspace ONE UEM enrollment as applicable. Whilst there are two options Enterprise Reset and Enterprise Wipe, the wipe option is disabled for cloud domain joined devices.
Once the device has been through either Windows Autopilot Reset or Windows 10 Enterprise Reset, the administrative team can then reassign the device to a new user in the relevant tool. This approach could be combined with a smart locker solution to create a user-driven device swap on failure service. On receipt, the new user authenticates to the device and the applications are re-provisioned from the software store provided by the MDM as before.
Alternatively, to provide a better user experience, a deployment engineer might use an on premises Windows Autopilot White Glove environment to pre-provision the device with those applications and configuration settings that can be targeted at the device. This may be particularly important in environments where Internet bandwidth is at a premium.
If you find this post useful or have ideas for other posts feel free to contact us via Twitter @modernEUC

